By Igino Corona, Chief Technology Officer & Security Researcher @ Pluribus One
The main goal of criminals can be summarized into one word: Money. Regardless local and international laws, they basically do whatever they can to (easily) make money and exploit it for their personal benefits.
Cybercriminals, i.e., criminal actors working on the virtual side of our world represent the biggest threat to Internet users.
As part of our mission for a better (safer) “virtual world”, we offer free DNS resolvers (see our Pluribus One Internet Security) and analyze the associated DNS traffic to detect and stop such threats.
Our detectors embed our expert knowledge of both DNS security and machine learning in the form of robust --adversary-aware-- measurements and classification models to generalize known threats and detect new threats.
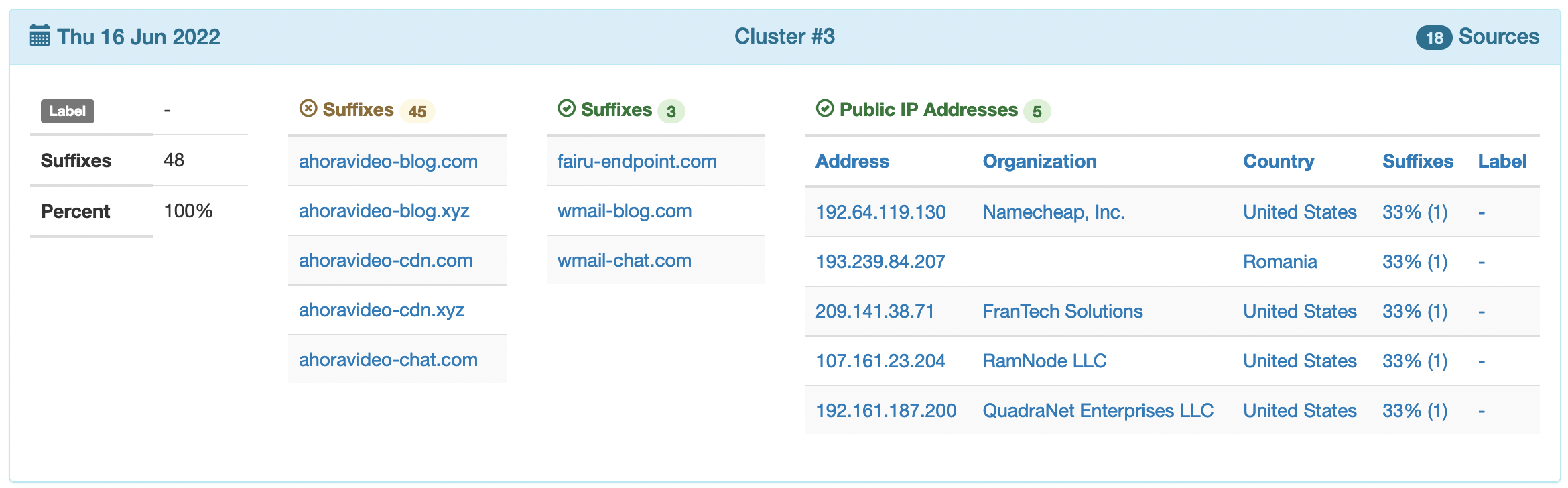
In this article we will delve into one relevant threat we are currently tracking by means of our passive DNS analysis, i.e., Powershell Cryptostealer Attacks. This is an excellent example of how network monitoring and (adversarial) machine learning can be exploited to detect new threats.