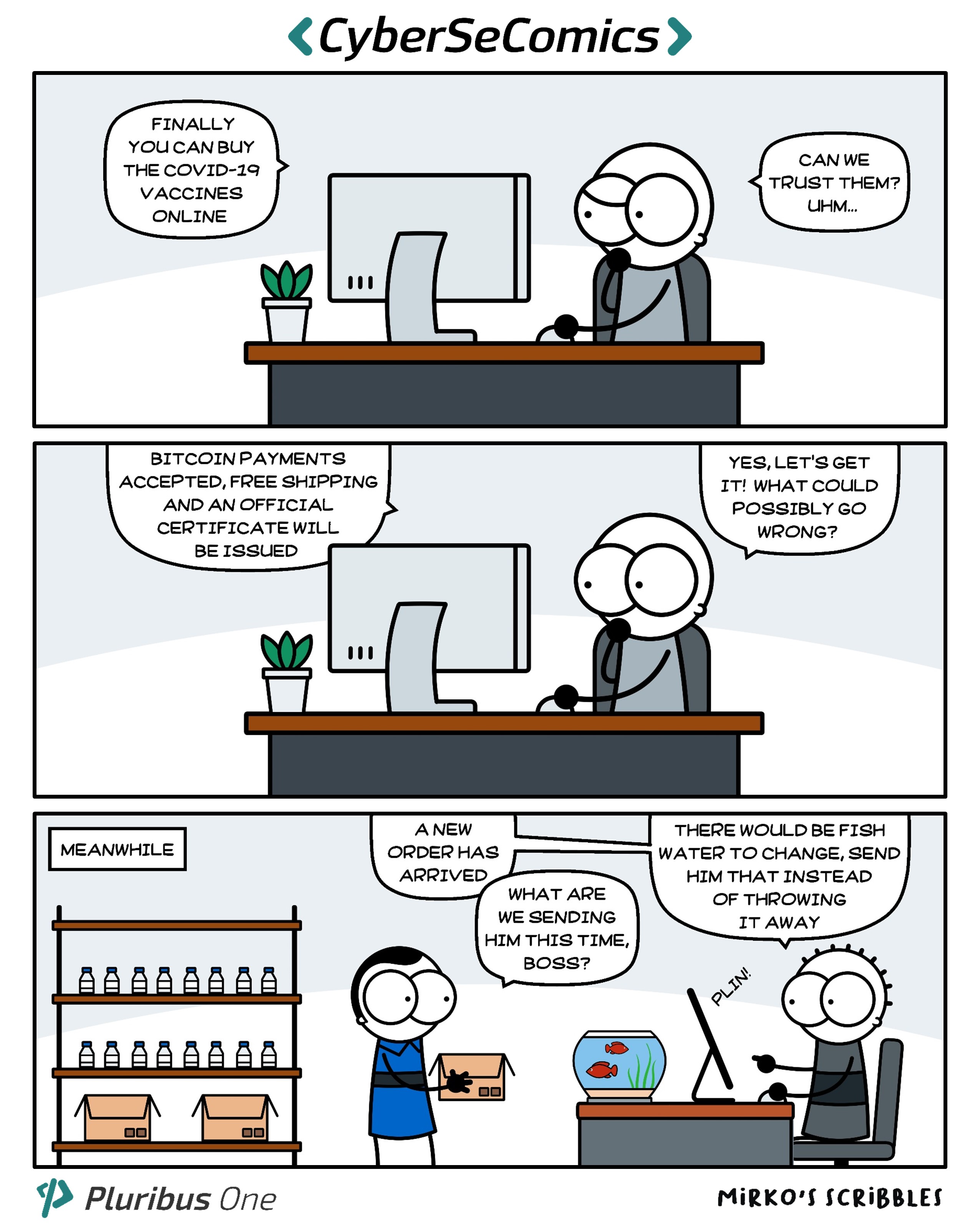
Seventh episode of CyberSeComics, comics series produced by Pluribus One.
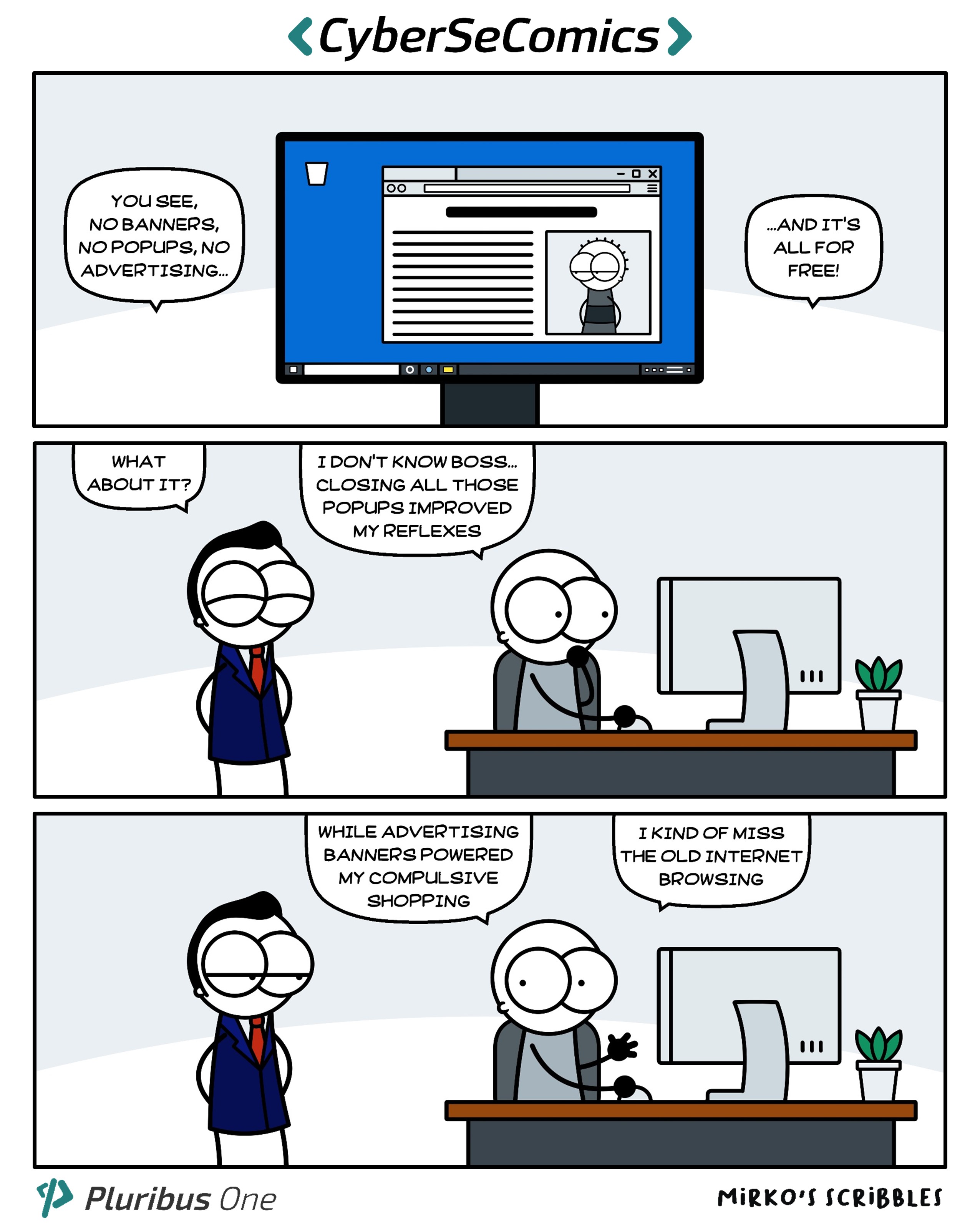
Prevention is better than cure! The more you spend the less you spend! Think Before ... You Click!
We agree with dentists and with all the proverbs that protect us from the consequences of a lack of planning, in our case from the consequences of a cyber attack. October has just ended: it was the European Cyber Security Month - ECSM (ECSM, organized by ENISA), a European Union campaign designed to promote awareness on cyber threats and methods to face them.
Wallo also wants to make his contribution to this campaign. Each data breach on organizations costs the impacted company on average 3.86 million dollars globally and 2.90 million euros in Italy. This according to Cost of a Data Breach 2020, a report conducted by Ponemon Institute on behalf of IBM Security, an organization that also notes a 10% increase in costs for the 2021.
Don't be like Wallo's boss! Be aware, invest in Cybersecurity!
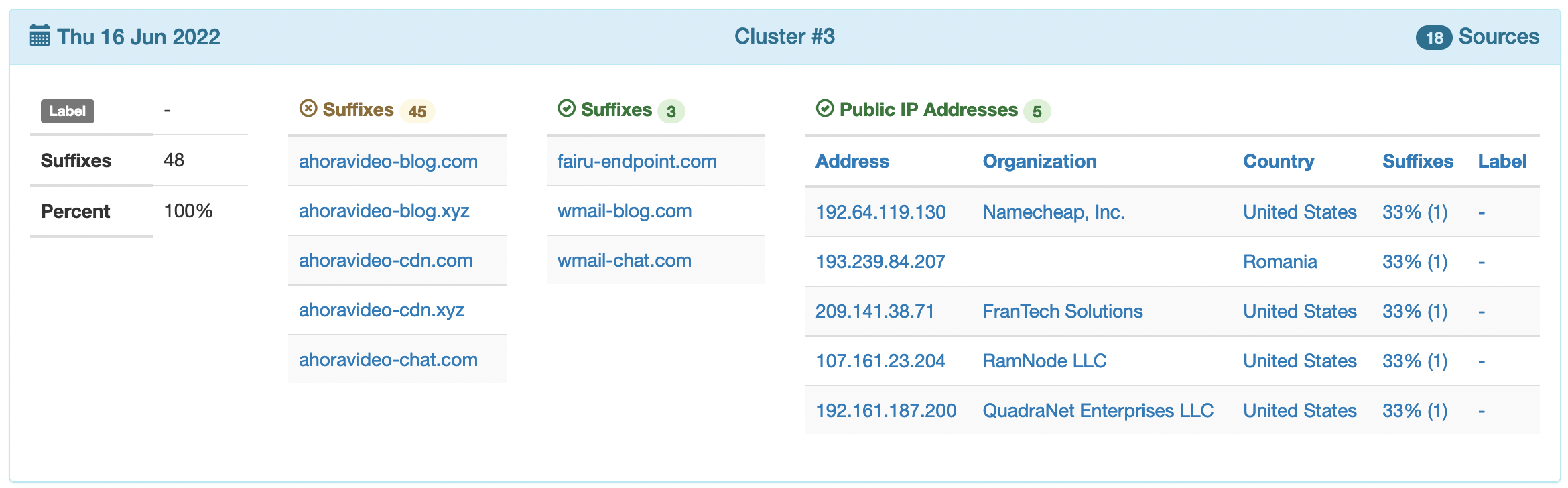
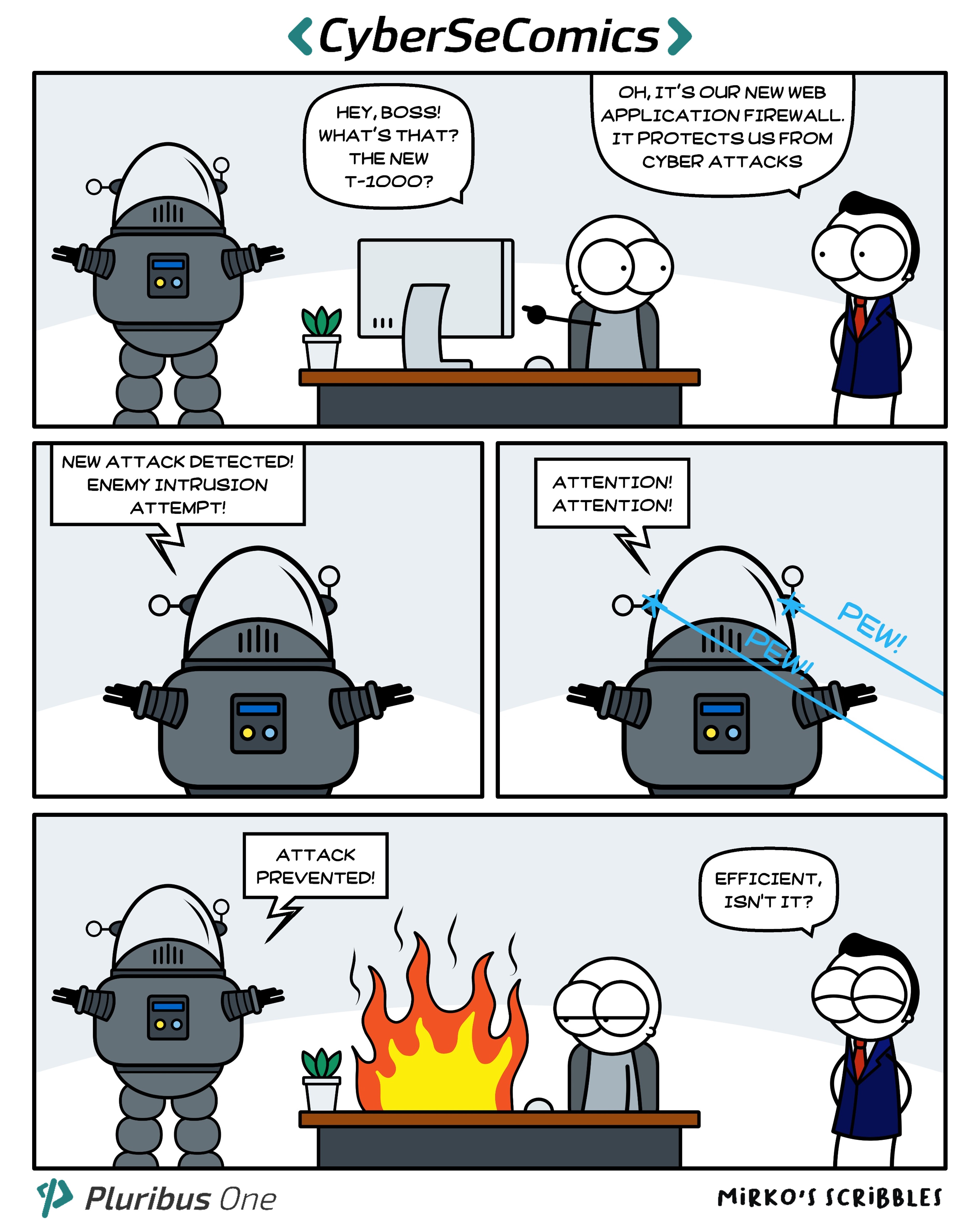
Pluribus One Web Application Security®, our solution for the protection of incoming traffic to web applications and services is smart and, thanks to sophisticated Machine Learning algorithms, tries to model the behavior of users who connect to the pages of a website, configuring a standard behavior profile. When we detect a behavior that deviates from the standard profile, the alarm is triggered.
The episode is available also in Italian language here: CyberSeComics Ep. #7 - Braccine corte.
Credits: Mirko's Scribbles (concept, storyboard, drawings); Matteo Mauri, Dissemination & Communication Manager at Pluribus One (idea, subject, concept).